A Complete Guide to Microsoft Entra Conditional Access
today’s world, organizations face ever-evolving security threats. Protecting sensitive data while ensuring users have seamless access to business resources is a challenge. Microsoft Entra Conditional Access provides a solution by allowing organizations to enforce adaptive policies based on real-time signals. This guide explores the history, features, setup, and latest updates in Conditional Access to help businesses strengthen their security posture.
This article will be bit longer than the other articles. Because I need to summarize all the details about Microsoft Entra Conditional Access Policies within a single post. So, I highly recommend you to read the complete article to get a solid understanding about Entra CA policies.
History of Conditional Access
Security started with simple
username-password authentication, but as cyber threats grew, businesses needed
stronger access control mechanisms. Role-Based Access Control (RBAC) and Single
Sign-On (SSO) were introduced to simplify and secure authentication, but they
were not enough to stop sophisticated attacks. With the rise of cloud computing
and remote work, organizations required dynamic security measures that adjusted
based on context. in order to fulfill this requirement, Microsoft introduced Conditional Access to address these
challenges by evaluating risk signals in real-time before granting access.
What is Microsoft Entra Conditional Access?
Microsoft Entra Conditional
Access is a policy-driven security framework that enables organizations to
control access to corporate resources. It considers signals such as user
identity, device status, location, and application sensitivity to determine whether
access should be granted, denied, or require additional authentication steps.
Entra ID Security Defaults
Since October 2019, Microsoft has been implementing Entra ID security defaults for newly created tenants. These defaults consist of pre-configured settings designed to defend against prevalent identity-based threats such as phishing and password spraying.
Security defaults are primarily intended for free-tier Entra ID tenants or those without access to Conditional Access features. Organizations with a P1 or P2 Entra ID licenses are advised to use Conditional Access policies instead of using security defaults. as it offers fully customizable security policies, whereas security defaults have fixed configurations.
How to check Entra ID’s Security Defaults
To enable Entra ID security
defaults:
- Sign in to the Microsoft Entra Admin Center as a security or higher level Admin.
- Navigate to Identity > Overview> Properties.
- Select Security Defaults and toggle it ON or OFF as per your need.
- Save changes to apply baseline security policies.
Types of Conditional Access Policies
- User-based policies – Applied based on user
groups or roles.
- Device-based policies – Enforced depending on
device compliance and trust level.
- Location-based policies – Access is allowed or
restricted based on geographic location.
- Application-based policies – Protects access
to specific applications based on sensitivity.
Features of Conditional Access Policies
- Adaptive authentication - to enhance security
while reducing friction.
- Granular access controls - for different users
and applications.
- Integration with risk-based authentication - to block suspicious logins.
- MFA enforcement - for added security layers.
Why You Should Adopt Conditional Access?
Conditional Access enhances security by ensuring that only legitimate users and devices are access business applications or any other corporate resources. It helps to prevent unauthorized access, secures remote work, and ensures compliance with industry regulations. So, let's talk about a real-life scenario...!!
Imagine you’re responsible for identity and access management in a Sri Lakan Company with 300 employees across various departments and places.
- R&D (some are working remotely).
- Sales (some are working in Australia).
- Accounting (some are working locally).
The company also outsources key services, such as:
- Security Operations Center.
- Marketing.
- IT and Cloud consulting.
Its infrastructure is a mix of on-premises and cloud environments, including:
- An on-premises Active Directory.
- Legacy on-premises applications.
- An Entra ID tenant synchronized with the on-prem AD.
- Workloads hosted on a major IaaS provider like Microsoft Azure.
- Cloud services and SaaS applications, including:
- Microsoft 365 (Email, SharePoint, Office, Teams, Office 365 Apps)
- Salesforce, Jira.
- GitHub.
- Accounting and finance SaaS solutions (Sage, Dynamics BC).
Given this setup, your challenge is to design a secure authentication strategy that balances security and usability, keeping in mind the following principles:
- Flexibility: Apply strict security measures only when absolutely necessary.
- Remote Work Support: Ensure every department can function remotely.
- Seamless Access: On-premises users should have Single Sign-On (SSO) across the hybrid environment.
- Role-Based Access Control: Employees should only access services relevant to their role.
- Least Privilege Principle: Grant minimal necessary permissions for each user.
This scenario reflects the reality of modern businesses, where employees work remotely across different locations with varying access levels. Strong authentication security is essential if an administrator or a user logs in from an unfamiliar location, their authentication process should be more stringent than when logging in from the office.
To achieve both flexibility and robust security, Conditional Access is key. It allows you to tailor security policies based on user roles, locations, and applications, creating a dynamic and secure authentication framework that meets your organization’s needs.
How Do Conditional Access Policies Work?
Conditional Access dynamically controls access to applications and resources based on specific conditions. It evaluates access requests in real-time, considering various factors like user identity, device compliance, location, risk level, and application sensitivity before granting or denying access.
When a user attempts to access a resource, Conditional Access follows a structured process.
Before making an access decision, Conditional Access gathers signals such as:
- User
Identity: Who is trying to log in? What is their role?
- Device
Health: Is the device compliant with security policies?
- Location:
Is the login coming from a trusted or unfamiliar region?
- Application
Access: Which application is being accessed?
- Risk Level: Does this login show signs of potential compromise (e.g., unusual location, multiple failed attempts)?
Once the contextual signals are collected, Conditional
Access evaluates them against the organization's pre-configured policies. These
policies define rules based on:
- Who is
trying to access (users/groups).
- Which
applications or services are being accessed.
- The
conditions under which access is requested (location, device, risk level).
- The
security controls required for access (MFA, device compliance, etc.).
After evaluating the request, Conditional Access enforces
one of the following actions:
- Grant
Access: If the request meets all security conditions, access is
granted.
- Require
Additional Authentication: If the login is from an unfamiliar location
or an untrusted device, Multi-Factor Authentication (MFA) may be required.
- Block
Access: If the request poses a high security risk (e.g., logging in
from a known malicious IP address, multiple sign failures, MFA failure), access will be denied.
Example Scenario
An employee attempts to access Microsoft 365 from an unknown device in a different country. Conditional Access would:
- Detect that the user is logging in from an unfamiliar location.
- Check if the device is compliant with security policies.
- Require MFA as an extra layer of security before granting access.
If this were an administrator logging in from an unusual location, stricter policies might apply, such as blocking access altogether or enforcing more advanced security measures.
How to Configure a Conditional Access Policy
Okay, now let's take a look on how to set up conditional access policies in your environment.
Here is the step-by-step guidance.
1. Access the Microsoft Entra Admin Center
- Sign
in to the Microsoft Entra admin center (entra.microsoft.com).
- Navigate to Identity > Protection > Conditional Access > Policies.
2. Create a New Policy
- Click +
New policy and give it a descriptive name (e.g., "MFA for
External Users").
3. Define Policy Conditions
- Assign Users or Groups: Select users, groups, or roles the policy applies to (e.g., all users, specific departments, or guest users).
- When assigning users or groups, please make sure to exclude a breakglass admin account which having enough admin permissions to the conditional access policy configuration to rollback the settings to previous to avoid unnecessary lockdowns.
- Select Target Resouces: Choose the resources that you want to
protect (e.g., All Cloud Apps, Global Secure Access, Specific App, User Action, Etc.).
- Set
Conditions, Network (Optional):
- Device
Platform (Windows, macOS, iOS, Android).
- Locations
(Block access from high-risk countries).
- Risk
Level (Enforce stricter rules for suspicious sign-ins).
4. Configure Access Controls
- Under Access
Controls, choose whether to:
- Block
access (e.g., deny access from unknown locations).
- Grant access with conditions (e.g., require Multi-Factor Authentication, a compliant device, or a trusted location, require to be marked as compliant, require approved client app, Require app protection policy).
5. Choose Policy Mode
- Report-only:
Test the policy without enforcing it.
- On:
Enable the policy immediately.
- Off:
Disable the policy while keeping it saved for future use.
6. Save and Deploy
- Click Create
to save and apply the policy.
- Monitor Sign-in logs to analyze how the policy affects users and make adjustments if needed.
By following these steps, administrators can create effective Conditional Access policies that enhance security while maintaining a seamless user experience.
What is Conditional Access Used For?
Now that we know which controls are configurable, it’s time to put them to use. Here’s how you can use Conditional Access controls to achieve your security and compliance goals.
- Preventing Unauthorized Access: To minimize the risk of account compromise, restrict access to only those using passwordless or phishing-resistant multi-factor authentication (MFA) methods.
- Location-Based Access Control: Manage access permissions based on where the authentication request originates. You can define trusted and untrusted zones with specific access rules. For instance, require MFA for users to log in from home while allowing seamless access from the company’s headquarters.
- Compliance-Based Access Control: Control access based on the device used for authentication. Different compliance conditions can be applied depending on the device’s status. For example, if a device is marked as compliant in Entra ID and is domain-joined, it can have more lenient controls compared to a Zero Trust-enforced policy.
- Session Management Controls: Adjust session duration based on user roles. By default, Entra ID sets reauthentication intervals at 90 days, but you can enforce stricter reauthentication requirements for specific roles. For example, administrators might be required to verify their identity more frequently than standard users.
- Granular Identity and Application Policies: Define highly specific access policies tailored to individual applications or users. For example, create a policy that grants access to an emergency administrator only under certain conditions, or enforce stricter authentication for critical applications like the Entra admin portal compared to other cloud services.
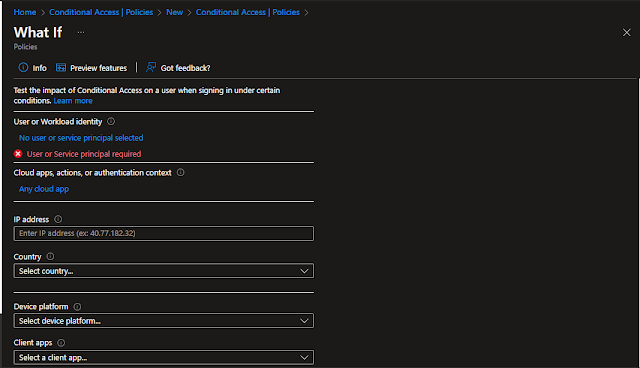
"What If" Feature in Conditional Access Policy?
The "What If" tool in Microsoft Entra Conditional Access is a powerful feature that allows administrators to simulate and test the impact of Conditional Access policies before enforcing them. It helps IT teams predict how specific users, groups, or sign-in conditions would be affected by existing policies, reducing the risk of unintended disruptions. So, lets see how it works.
How It Works
- Access
the Tool: Navigate to the Microsoft Entra admin center → Identity
→ Protection → Conditional Access → Policies → What If.
- Enter
Test Parameters: Select a specific user, application, device,
location, and other conditions to simulate an access scenario.
- Run
the Simulation: The tool evaluates existing Conditional Access
policies and displays which policies would apply, whether access would be
granted or denied, and if additional authentication (like MFA) would be
required.
- Analyze
Results: IT admins can review the expected enforcement outcomes and
adjust policies if needed before applying them to real users.
Why Use the "What If" Tool?
- Prevents
Lockouts: Ensures that legitimate users are not accidentally blocked.
- Speeds
Up Troubleshooting: Helps diagnose why a policy is or isn’t applying
as expected.
- Refines
Policies: Allows fine-tuning of policies to achieve the right balance
between security and usability.
In short, the "What If" feature provides a risk-free
way to evaluate Conditional Access policies, making it an essential tool
for managing access control effectively
Latest Features of Conditional
Access Policy
Microsoft continuously improves
Conditional Access with features such as:
- AI-driven risk assessments.
- Enhanced session controls for cloud apps.
- New integrations with Microsoft Defender for threat
protection.
Testing and Troubleshooting
If a Conditional Access policy isn’t working as expected—blocking legitimate users, not applying correctly, or causing unexpected authentication issues, here are some effective troubleshooting methods.
1. Use the
'What If' Tool
The "What If" analysis tool
helps simulate access scenarios and predict which policies will apply to a
specific user.
- Go to Microsoft
Entra admin center → Protection → Conditional
Access → Policies → What If.
- Enter
user details, location, application, and device info.
- Review
which policies apply and adjust as necessary.
2. Review
Sign-In Logs
Sign-in logs provide real-time insights into why
a Conditional Access policy is enforced or blocked.
- Navigate
to Microsoft Entra admin center → Identity → Monitoring
& Health → Sign-in Logs.
- Select a
user sign-in attempt and review:
- Authentication
details
- Applied
Conditional Access policies
- Reasons
for access denial or MFA prompts
- Use the "Conditional
Access" tab in the logs to see which policies affected the sign-in.
3. Check
Policy Settings
Misconfigured policies can cause unexpected
behavior. Review:
- User
Assignments: Ensure the right users/groups are included
or excluded.
- Application
Selection: Verify that the correct apps are covered
by the policy.
Conditions & Controls: Check if location, device compliance, or risk-based settings are too restrictive
4. Enable
Report-Only Mode Before Enforcing Policies
- Instead
of applying a policy immediately, use Report-Only mode to test its
impact without enforcement.
- Go to Conditional
Access policies, edit the policy, and set the Enable Policy
option to Report-only.
- Monitor
sign-in logs to see how the policy behaves before enabling enforcement.
5. Check for
Conflicting Policies
Multiple Conditional Access policies may overlap
and cause conflicts.
- Review
all active policies to ensure there’s no contradiction between different
rules.
- Use policy
precedence to determine which policy takes priority.
6. Verify MFA
and Device Compliance Settings
If users are unexpectedly blocked or prompted for
MFA, check:
- Entra ID
Security Defaults: If enabled, they might conflict with
Conditional Access MFA policies.
- Device
Compliance Policies: Ensure the correct compliance settings are
applied for managed devices.
7. Test with
Different User Scenarios
- Try
logging in from different locations, devices, and network conditions to
see how policies behave.
- Use a test
account to safely experiment with policy changes.
8. Use
Conditional Access Insights & Reporting.
- In Microsoft
Entra admin center, navigate to Workbooks → Conditional
Access Insights and Reporting.
- Analyze
the data to identify policy misconfigurations, failed sign-ins, and
risk-based decisions.
9. Temporarily
Disable or Modify the Policy.
If a policy is too restrictive, consider:
- Disabling
it temporarily to test whether it’s causing the issue.
- Adjusting
conditions to make access rules more appropriate.
10. Seek
Microsoft Support
If all troubleshooting steps fail, consult Microsoft
documentation or open a support ticket with Microsoft.
Conclusion
Now we went through a fully detailed walkthrough about Microsoft Entra Conditional
Access policies. This is a powerful tool for securing business resources while ensuring a
seamless user experience. By implementing well-structured policies,
organizations can strengthen security, enhance compliance, and embrace a Zero
Trust security model. Ready to implement Conditional Access? Start configuring
your policies today and take your security to the next level.
If you want to have a deep dive into Microsoft SSE. refer these official Microsoft documentation and guides:
Microsoft Entra Conditional Access documentation - Microsoft Entra ID | Microsoft Learn
Have thoughts or questions? I'd love to hear from you! Drop a comment below, and let's discuss more…!!!
Also, I would like to invite you to read my other articles as well:












0 Comments