How to Use Microsoft Defender Attack Simulation Training to Strengthen
Organization’s Security
When it comes to cybersecurity, one of the biggest threats isn't a fancy virus or a sophisticated exploit, it's people. Not because they're careless, but because attackers are getting better at tricking even the most tech-savvy of us. That’s where Microsoft Defender Attack Simulation Training comes in.
I’ve used this tool in my organization to run real-world phishing simulations, test user responses, and follow up with tailored training. In this post, I’ll Walk you through what it is, why it matters, how to set it up, and how we can see it work in practice.
What is Microsoft Defender Attack Simulation Training?
At its core, Attack Simulation
Training is a built-in feature of Microsoft Defender for Office 365 (Plan
2) that lets us safely simulate cyberattacks like phishing or malware emails to
see how users respond. Think of it as fire drills for phishing: we send
realistic (but safe) attacks, observe behavior, and offer training where
needed.
Here are the Key Features of Microsoft Defender Attack
Simulation Training
- Simulates different kinds of social engineering attacks.
- Provides analytics to identify vulnerable users.
- Automatically assigns security training based on user behavior.
- Fully integrated into the Microsoft Defender portal.
Okay then. Now let’s talk about what
are the key benefits of using Attack Simulation Training.
Benefits of Using Attack Simulation Training
Security Awareness
Let’s say, many users may assume
phishing is obvious. After running a few simulations, they can realize how
subtle and convincing some scams can be. So, it’s like an eye-opener and then
organizations can more focus on identity-based security.
Risk Management
We will be able to spot
departments or roles that are more frequently targeting or more likely to fall
for certain types of attacks (e.g., credential harvesting). This helps organizations
to adjust the defenses and security counter measures accordingly.
Compliance
Some regulatory frameworks
require regular security awareness training. This platform helps organizations and
their IT teams to meet those requirements while also proving their efforts
through built-in reporting.
Okay guys, Here comes the most
important part. Now we are going for a walkthrough on How to Get Start with M365
Defender Attack Simulation Training. So, let’s go for it.
How to Get Started
Requirements:
To use Attack Simulation
Training, you’ll need one of the following licenses.
- Microsoft 365 E5 license OR
- Microsoft Defender for Office 365 Plan 2 (add-on)
And you also need appropriate
permissions.
- Global Administrator
- Security Administrator
Or roles specific to simulations
like Attack Simulation Administrator if you like to go with least privileges.
Setup Steps:
- Go to the Microsoft Defender Portal.
- In the left pane, navigate to Email &
Collaboration > Attack Simulation Training.
- Click Launch a Simulation and follow the
guided setup.
- Choose a technique (e.g., phishing), select your
payload, and define your target audience.
- Schedule the simulation for specific time period or
run it immediately.
 |
| Overview Page |
Note: The mentioned steps
are the general way to perform a simulation. But there are many more things
that are a bit hard to discuss through a single blog post. So, I will try my
best to summarize details for a better understanding of all readers.
You also can refer the official Microsoft
Documentation about Attack Simulation Training to get all the necessary
details that you need to know.
Okay, so let’s talk about what
are the types of Simulations that we can run within our environment.
Phishing Attacks
These simulate emails that mimic
delivery notifications, bank alerts, or urgent security warnings. We use both
simple and highly targeted phishing templates to test how users react.
Other Techniques:
- Credential Harvesting: Fake login pages that
mimic Microsoft 365 or Dropbox or LinkedIn.
- Malware Attachments: Emails with “invoices”
that, if opened, simulate malware execution.
- Drive-by URLs: Links that simulate background
malicious activity when clicked.
- OAuth Consent Grant: Simulates malicious apps
requesting unauthorized permissions.
Each type targets different user
behaviors, which gives us insight into where our defenses are weakest. As I
previously said, these are the points that we need to put more focus on.
Now we are going to run a Simulation.
So, let’s look at how it works and what are the things that we need to configure
and perform during the simulation.
Creating a Simulation
Microsoft provides a guided wizard that makes it pretty easy.
- Choose your attack technique and give a name to your simulation.
 |
| Select Attack Technique |
- Pick a payload template or create a custom one.
 |
| Select the Payload Template |
- Define your target group by adding users or groups. Or you can add all users in the organization at the same time.
 |
| Select the Targets |
- You can exclude specific users as per your requirement.
- Select the Training types that need to be enrolled for users who compromised their users accounts.
 |
| Select the Training Type |
- Choose the Phish landing page. You can use Microsoft provided landing pages or also can use custom URLs if you have.
 |
| Choose a Phishing Landing Page |
- Select the user notification level about the Simulation
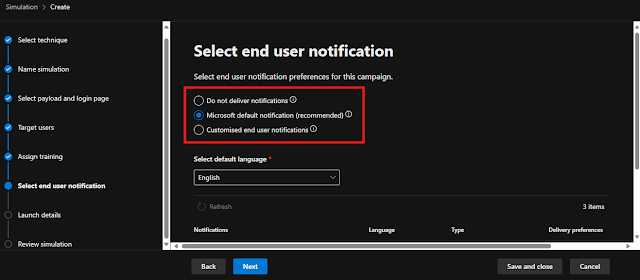 |
| Choose User Notifications |
- Decide how long the simulation should run.
 |
| Decide the Deployment of the Simulation |
- Review and submit the Simulation and it will formulate based on your selections.
 |
| Review the configurations before Submitting |
Customizing Simulations
You can often tweak the timing,
sender name, and look of the phishing emails to make them more relevant to your
organization (e.g., mimicking your actual help desk team). You can also upload
custom payloads or even QR code phishing links.
Training and Reporting
Okay guys, now we have done the
simulation. The users who fall for a simulation (like clicking a link or
entering credentials) automatically enroll in training modules. These are
bite-sized, interactive, and designed to improve future responses.
Finally, it will generate a
report on the Simulation outcomes. In this post-simulation report, we can see
these details in a dashboard view.
- Click rates
- Credential entry rates
- Users who completed training
- Repeat offenders
Now, it’s time
to review the report of the simulation and submit it to your Information
Security Officer, Head of IT or any other person who is mainly looking for IT
security. Also, this data is gold for tailoring your security awareness
strategy.
Best Practices
Run Regular Simulations
We can run at least one campaign
per quarter. The idea is to build a culture where users stay alert, not just
right after training but continuously.
Engage Your Users
We must always communicate the
purpose clearly. This isn’t about catching anyone out. It’s about helping
everyone stay safer. After each campaign, we can debrief and share anonymized
stats and lessons learned.
Continuously Improve
I think ee don’t need to repeat
the same simulations. We can rotate attack styles, tweak payloads, and expand
our training library. The more varied, the more effective.
Conclusion
If you’re using Microsoft 365 and
are not leveraging Attack Simulation Training, you’re missing a huge
opportunity to improve your cyber resilience. It’s one of the most practical,
hands-on ways to strengthen your weakest link. your people…!!!
So, take the first step. Try a
simple simulation, learn from it, and keep building.
Additional Resources
Have you gone through this Simulation ever? I’d love to hear about your experiences and any additional insights you might have!
Also, I would like to invite you to read my other articles as well:










0 Comments